-
Poster Presentation
-
-
-
Machine Learning is just a fancy term for Statistics.
And to get through ML, one needs a good understanding of Linear Algebra, Calculus and Probability Theory.
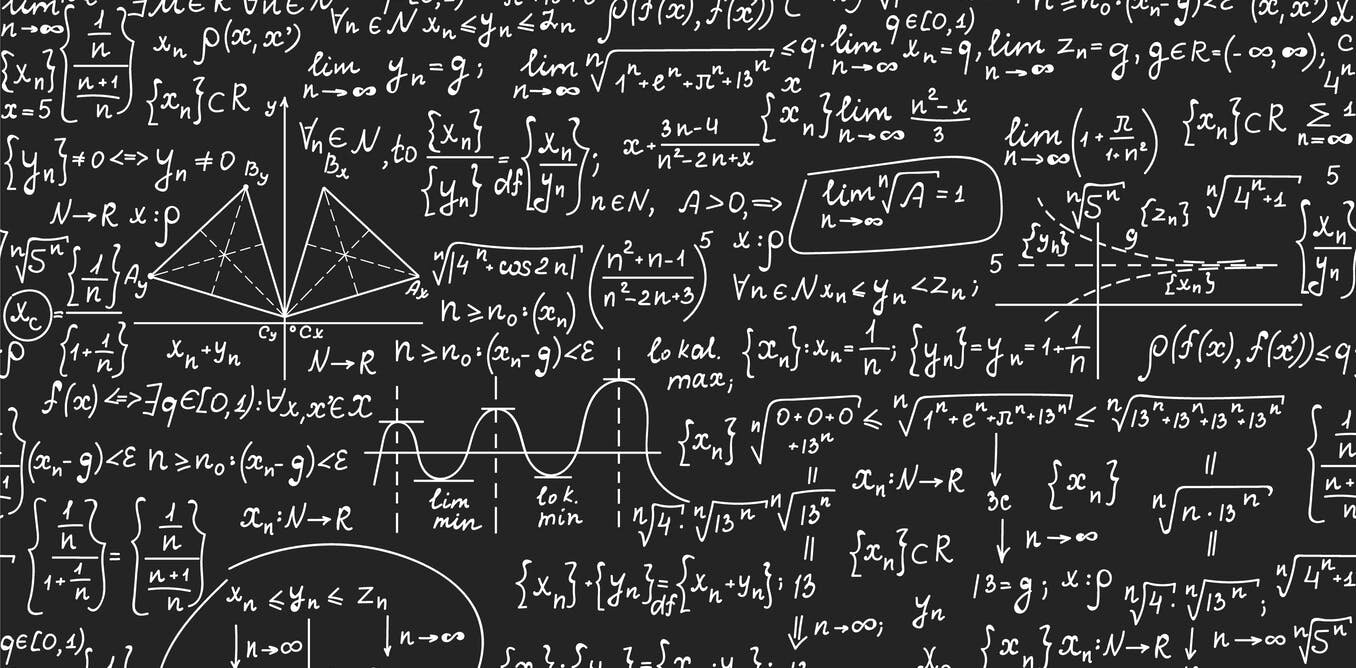
Thus, I have composed a quick cookbook for all the mathematical concepts required for data analysis and statistical modeling.
Predicting bitcoin prices using ensembling on multivariate time series. These feature sets can be categorised as macroeconomic factors, blockchain attributes and public opinion.
I have been coding in Python, on and off, for 5 years now. Yet every time I am about to start a new project, I look for those quick recap videos on YouTube. But none seems to cater my explicit requirements, thus after a long overhaul, I came up with my version of a Python notebook that covers the topics relevant to the analytics domain.
Predicting pedestrian hot-spots in the city of Melbourne for street art performers. The predictions were made on real time streaming data using Apache Kafka and Spark.
While people are busy learning about the much hyped Python and R programming languages, they often neglect the basic querying concepts. And without a database, Data Science seems quite meaningless.
Predicting the spread of COVID like Virus among social connections using OOP concepts and Probability Theory.
Explored data from Parking Sensors across the city of Melbourne using Tableau and Visualised the results via a dynamic website built using Shiny in R.
Categorised 50,000 Research Papers using Natural Language Processing and Topic Modelling.
Deployed 24 different configurations to compare Statistical Modelling against Deep Learning for Natural Language Processing.
Case Study to build an application to find available Parking Bays in Melbourne.
Petya, generally, is the term for a ransomware program which targets Microsoft Windows based systems by infecting the MBR and demands virtual money to release the files uninfected.
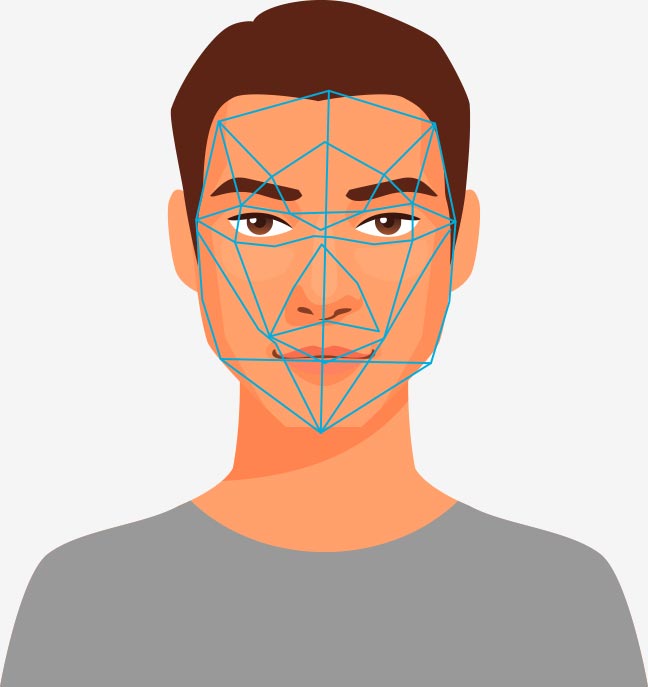
Detecting and identifying faces using KNearestNeighours and Haar Cascades.
Growing organisations face a number of issues ranging from investing in technology to taking appropriate measures to secure it. As the business grows, it demands enhanced security layers and better solutions for newer problems.
Security-Intelligence refers to real time monitoring and analysis of critical data that has the potential to impact an organisation, both in terms of reputation as well as capital.
Cloud computing is comparatively new but tends to hold great potential in terms of upcoming applications. Keeping its benefits aside, let’s start from the base level to rule out the better alternative among Cloud and Physical servers.
End to end encryption is an enforced algorithm for communication between two endpoint devices, to prevent a third party from accessing the packets between these clients.
Mined over a million movie reviews using a variety of Machine Learning models.
Data Loss Protection is the practice followed to restrict movement of data outside the organisation and is highly recommended to avoid misuse of proprietary information or other sensitive material.
Using classification to improve diabetes diagnostics by computing factors that may affect insulin levels.
After acquiring Whole Foods for a whooping $13.7 Billion, Amazon drops another bomb by patenting a new technology to restrict its customers from comparing rival’s products, while in amazon stores.
A website to report items lost and/or found in college, built using Bootstrap, MySql and PHP.
Developed a website to share academic material like notes, eBooks and projects.
A zip bomb, also known as a zip of death or decompression bomb, is a malicious archive file designed to crash the program or system reading it.
Full duplex communication channel between Server and Client by binding sockets in C.
Acronyms SaaS, PaaS and IaaS are heavily used in cloud computing industries and are the models for online services that a cloud offers. The “Cloud” is a very broad concept otherwise but let’s just focus on a few services that it offers.
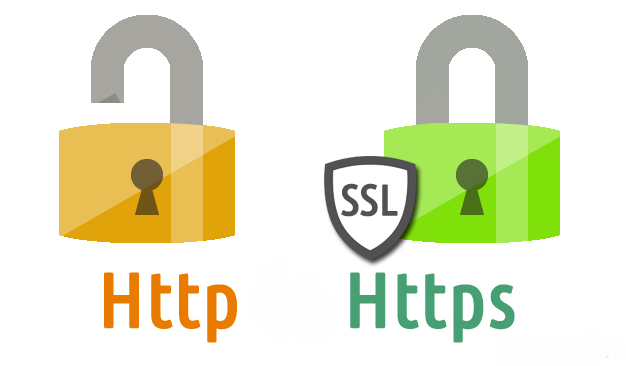
HTTP stands for HyperText Transfer Protocol and is used to control the transfer of content over the web. The content may vary from miniature texts to heavy graphic files. This protocol was developed by Ted Nelson and came out in 1991 with its successors in 1996, 1997 and 2015.
USBs have been a very part of our computing needs but only a few of us would be knowing what it stands for. And that’s Universal Serial Bus. Going by it’s nomenclature, type-C looks like a bump to the trend for standardising the connection peripherals. For those, still unaware of the new form-factor of the USB port, here’s the visual to explain why is USB type-C a big deal!
Assembled an online tool to browse, categorise and add new books.
Question arises, how domain extensions work and what impact do these have on the internet market. For all the curious minds out there, here’s a list of the existing common extensions:
- .com
- .net
- .org
- .in
- .us
- .xyz
- .website
A fork bomb aka Rabbit Virus is a denial-of-service attack wherein a process continually replicates itself to deplete available system resources, slowing down or crashing the system due to resource starvation.